The Evolving Threat: Cybersecurity in the Age of Free Online Games
Related Articles: The Evolving Threat: Cybersecurity in the Age of Free Online Games
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Evolving Threat: Cybersecurity in the Age of Free Online Games. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Evolving Threat: Cybersecurity in the Age of Free Online Games
- 2 Introduction
- 3 The Evolving Threat: Cybersecurity in the Age of Free Online Games
- 3.1 The Rise of Free-to-Play and Its Implications
- 3.2 The Cybersecurity Landscape in 2025
- 3.3 Mitigating the Risks: A Multifaceted Approach
- 3.4 FAQs:
- 3.5 Tips:
- 3.6 Conclusion:
- 4 Closure
The Evolving Threat: Cybersecurity in the Age of Free Online Games

The digital landscape is constantly evolving, and with it, the threats to our online security. While the allure of free online games remains a potent draw, it also presents a potential gateway for malicious actors. This article explores the evolving nature of cybersecurity threats in the context of free online games, highlighting the vulnerabilities, potential consequences, and strategies for mitigating risks.
The Rise of Free-to-Play and Its Implications
The gaming industry has witnessed a significant shift towards free-to-play models, fueled by the accessibility and affordability they offer. While this has democratized gaming and brought it to a wider audience, it has also created new avenues for cybercriminals. Free-to-play games often rely on advertising revenue and in-game purchases, making them attractive targets for malicious actors seeking to exploit these revenue streams.
Vulnerabilities:
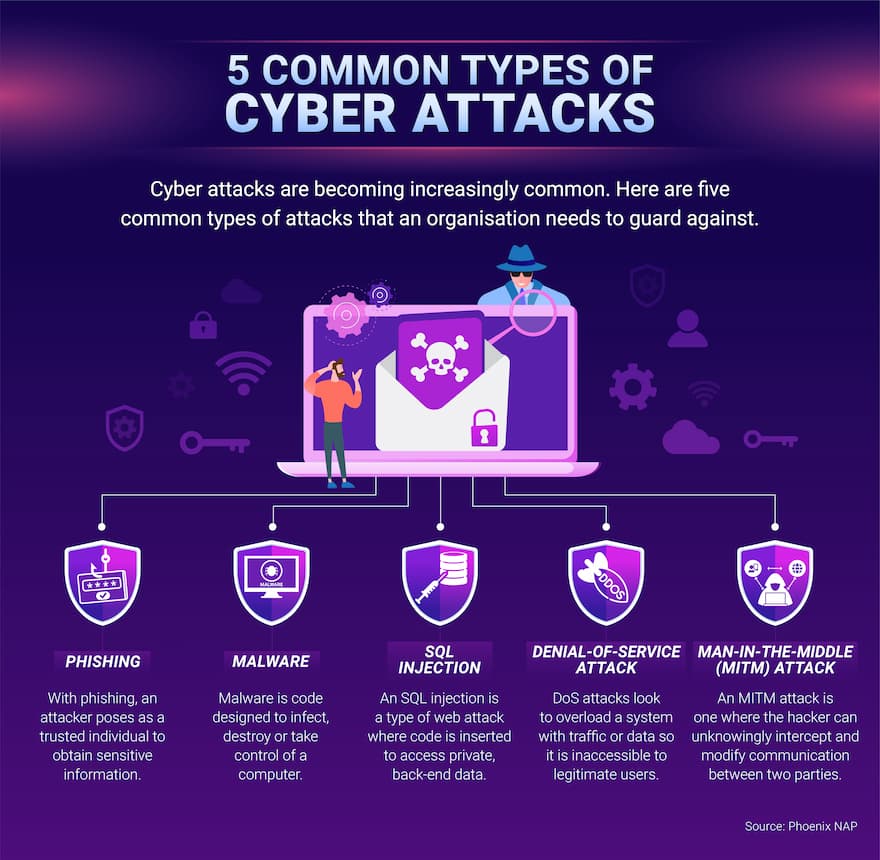
- Data Collection and Privacy: Free-to-play games often require extensive user data for personalized advertising and gameplay experiences. This data, if compromised, can be misused for identity theft, targeted phishing campaigns, or even blackmail.
- In-Game Currency and Items: Virtual currencies and in-game items hold real-world value for some players, making them lucrative targets for hackers. Stolen accounts or compromised virtual assets can result in financial losses for players.
- Malware Distribution: Free online games can serve as vectors for distributing malware, such as Trojans, viruses, and ransomware. These malicious programs can steal sensitive information, disrupt system operations, or even hold data hostage for ransom.
- Social Engineering: Hackers often employ social engineering tactics to manipulate players into revealing personal information or granting access to their accounts. This can involve creating fake giveaways, using deceptive links, or impersonating trusted individuals.
The Cybersecurity Landscape in 2025
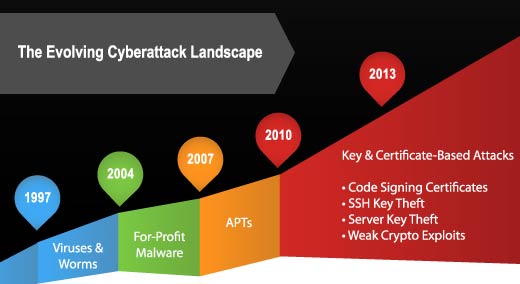
Looking ahead to 2025, the cybersecurity threats associated with free online games are likely to become more sophisticated and pervasive.
- Advanced AI-Powered Attacks: Artificial intelligence (AI) will likely play a more prominent role in cyberattacks, enabling more targeted and efficient exploitation of vulnerabilities. AI-powered malware can adapt to security measures, making detection and mitigation more challenging.
- The Rise of the Metaverse: The emergence of virtual reality (VR) and augmented reality (AR) technologies will create new opportunities for cybercriminals. Metaverse environments will offer a more immersive experience, potentially increasing the risk of phishing attacks, social engineering, and data breaches.
- Increased Use of Mobile Devices: The growing popularity of mobile gaming presents new vulnerabilities, as mobile devices are often less secure than desktop computers. Mobile gaming platforms may lack robust security measures, making them susceptible to malware and data breaches.
Mitigating the Risks: A Multifaceted Approach
Addressing the cybersecurity threats associated with free online games requires a multifaceted approach involving both individual users and game developers.
Individual Users:
- Choose Reputable Platforms: Opt for well-established and reputable gaming platforms with a proven track record of security.
- Strong Passwords and Two-Factor Authentication: Utilize strong, unique passwords for each account and enable two-factor authentication for an extra layer of security.
- Be Wary of Suspicious Links and Offers: Do not click on suspicious links or download files from unknown sources. Be skeptical of offers that seem too good to be true.
- Keep Software Updated: Regularly update operating systems, antivirus software, and game clients to patch vulnerabilities and enhance security.
- Be Mindful of Privacy Settings: Review and adjust privacy settings in games and on gaming platforms to limit the amount of personal information shared.
- Educate Yourself: Stay informed about the latest cybersecurity threats and best practices for online safety.
Game Developers:
- Robust Security Measures: Implement comprehensive security measures, including encryption, access controls, and intrusion detection systems.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
- Data Protection and Privacy: Adhere to data protection regulations and implement strong privacy policies to safeguard user information.
- Transparency and Communication: Communicate security measures and policies clearly to players, fostering trust and transparency.
- User Education and Awareness: Provide users with educational resources and guidance on online safety and security best practices.
FAQs:
Q: Can I trust free online games?
A: While many free online games are safe and enjoyable, it is important to exercise caution and be aware of potential risks. Choose reputable platforms and games, and practice good online safety habits.
Q: How can I protect myself from malware?
A: Use a reputable antivirus program, keep your software updated, and avoid downloading files from unknown sources. Be cautious of suspicious links and attachments.
Q: What should I do if I think my account has been compromised?
A: Change your password immediately and contact the game developer or platform provider to report the incident. If you have made in-game purchases, consider contacting your bank or credit card company.
Q: What are some signs of a phishing attempt?
A: Look for suspicious links, misspelled website addresses, urgent requests for personal information, and offers that seem too good to be true.
Q: How can I stay informed about cybersecurity threats?
A: Follow reputable cybersecurity news sources, subscribe to security alerts from your operating system and antivirus software, and participate in online security forums.
Tips:
- Use a separate email address for gaming: This helps protect your primary email from spam and phishing attempts.
- Enable parental controls: If you are playing with children, use parental controls to restrict access to inappropriate content and limit in-game spending.
- Be cautious when using public Wi-Fi: Avoid accessing sensitive information or making online purchases while using public Wi-Fi networks.
- Report suspicious activity: If you encounter any suspicious activity or encounter a scam, report it to the game developer or platform provider.
Conclusion:
The evolving nature of cybersecurity threats in the context of free online games underscores the importance of vigilance and proactive measures. By understanding the vulnerabilities, potential consequences, and strategies for mitigation, individuals and game developers can work together to create a safer and more secure gaming environment. A collective effort to educate, empower, and implement robust security practices is essential to protect players and safeguard the future of online gaming.






Closure
Thus, we hope this article has provided valuable insights into The Evolving Threat: Cybersecurity in the Age of Free Online Games. We appreciate your attention to our article. See you in our next article!