The Evolving Landscape of Game Security: A Look at Potential Vulnerabilities in 2025
Related Articles: The Evolving Landscape of Game Security: A Look at Potential Vulnerabilities in 2025
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Evolving Landscape of Game Security: A Look at Potential Vulnerabilities in 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Evolving Landscape of Game Security: A Look at Potential Vulnerabilities in 2025

The gaming industry, a multi-billion dollar behemoth, is constantly evolving. Advancements in technology, particularly in the realm of artificial intelligence (AI), have spurred innovation in game development, leading to immersive and complex experiences. However, this evolution also presents new challenges, particularly in the realm of cybersecurity.
While the focus on game security has increased, the landscape remains dynamic, with new vulnerabilities emerging alongside the introduction of novel technologies. This article delves into the potential vulnerabilities and security challenges that games might face in 2025, highlighting the importance of proactive security measures.
Understanding the Dynamics of Game Hacking
Game hacking, the unauthorized modification of game software for personal gain, is a persistent threat. Hackers exploit vulnerabilities in game code, server infrastructure, or client-side applications to gain unfair advantages, steal in-game assets, or disrupt gameplay.
Potential Vulnerabilities in 2025
The following are some potential vulnerabilities that could be exploited in games by 2025:
- AI-Powered Hacking: The increasing adoption of AI in game development presents both opportunities and challenges. While AI can enhance gameplay and improve security measures, it also introduces potential vulnerabilities. Hackers might exploit AI algorithms to generate sophisticated cheat codes, bypass anti-cheat systems, or even manipulate game logic to gain an unfair advantage.
- Cloud Gaming and Distributed Systems: The rise of cloud gaming platforms, where games are streamed from servers to devices, introduces new vulnerabilities. Hackers could target cloud infrastructure, potentially impacting the integrity and security of game data, gameplay, and user accounts.
- Blockchain Technology and NFTs: The integration of blockchain technology and non-fungible tokens (NFTs) in games opens up new avenues for hacking. Hackers could exploit vulnerabilities in smart contracts, leading to the theft of valuable in-game assets or manipulation of game economies.
- Cross-Platform Play and Interoperability: The growing trend of cross-platform play, allowing players on different platforms to interact, presents unique challenges for security. Hackers could exploit differences in security protocols across platforms, potentially compromising player accounts or disrupting gameplay.
- Emerging Technologies: The rapid pace of technological advancements introduces new vulnerabilities. For example, the integration of augmented reality (AR) and virtual reality (VR) into games could create new attack vectors for hackers.
The Importance of Proactive Security Measures
To mitigate these potential vulnerabilities, game developers must prioritize proactive security measures:
- Robust Security Testing: Regular security audits and penetration testing are crucial to identify and address vulnerabilities before they can be exploited. This includes evaluating code, server infrastructure, and client-side applications for potential weaknesses.
- Anti-Cheat Systems: Advanced anti-cheat systems are essential for detecting and preventing cheating. These systems should be constantly updated to stay ahead of evolving hacking techniques.
- Secure Code Development: Developers should follow secure coding practices to minimize vulnerabilities in game code. This includes using secure libraries, avoiding common coding errors, and implementing security measures throughout the development lifecycle.
- Strong Authentication and Authorization: Robust authentication and authorization mechanisms are critical for protecting user accounts and sensitive data. This includes multi-factor authentication, secure password management, and access control measures.
- Data Encryption and Security: Sensitive game data, such as user information and in-game assets, should be encrypted both in transit and at rest. Secure storage practices and data loss prevention measures are also crucial.
- Threat Intelligence and Monitoring: Game developers should stay informed about emerging hacking techniques and threats. This includes monitoring online forums, hacker communities, and security research to identify potential vulnerabilities.
- Collaboration with Security Experts: Engaging with cybersecurity professionals can provide valuable insights and expertise to enhance game security. This includes collaborating with security researchers, penetration testers, and anti-cheat specialists.
FAQs
1. What are the most common types of game hacks?
Common game hacks include:
- Cheats: Modifying game code to gain unfair advantages, such as unlimited resources, invincibility, or faster movement.
- Bots: Automated programs that perform repetitive tasks in-game, such as grinding for resources or killing players.
- Exploits: Using vulnerabilities in game code to gain access to sensitive data or manipulate game logic.
- DDoS Attacks: Flooding game servers with traffic to disrupt gameplay and cause outages.
2. How can I protect myself from game hacks?
- Use strong passwords: Avoid using easily guessable passwords and enable multi-factor authentication whenever possible.
- Be cautious of suspicious links and downloads: Don’t click on links or download files from unknown sources.
- Keep your game and operating system updated: Updates often include security patches that address known vulnerabilities.
- Use reputable anti-virus software: Anti-virus software can help detect and remove malware that could compromise your system.
- Avoid sharing personal information: Be wary of phishing scams and avoid sharing personal information on untrusted websites.
3. What are the consequences of game hacking?
- Account suspension or ban: Game developers often take action against players caught cheating.
- Loss of in-game assets: Hackers can steal valuable in-game items or currency.
- Damage to reputation: Cheating can damage a player’s reputation within the gaming community.
- Legal consequences: In some cases, game hacking can be a criminal offense.
4. How can I report game hacks?
Most game developers provide methods for reporting hacking and cheating. Check the game’s official website or support forums for information on how to report suspicious activity.
Tips for Developers
- Prioritize security from the start: Integrate security considerations into the game development process from the beginning.
- Embrace a culture of security: Encourage developers to be aware of security risks and best practices.
- Continuously monitor and adapt: Regularly review security measures and adapt them as needed to address new threats.
- Collaborate with the gaming community: Engage with players to gather feedback on security issues and potential vulnerabilities.
Conclusion
The gaming industry is facing increasing cybersecurity challenges as games become more complex and interconnected. Proactive security measures are essential to protect players, maintain game integrity, and foster a fair and enjoyable gaming experience. By adopting a comprehensive approach to game security, developers can mitigate vulnerabilities, prevent hacking, and ensure a secure future for the gaming industry.


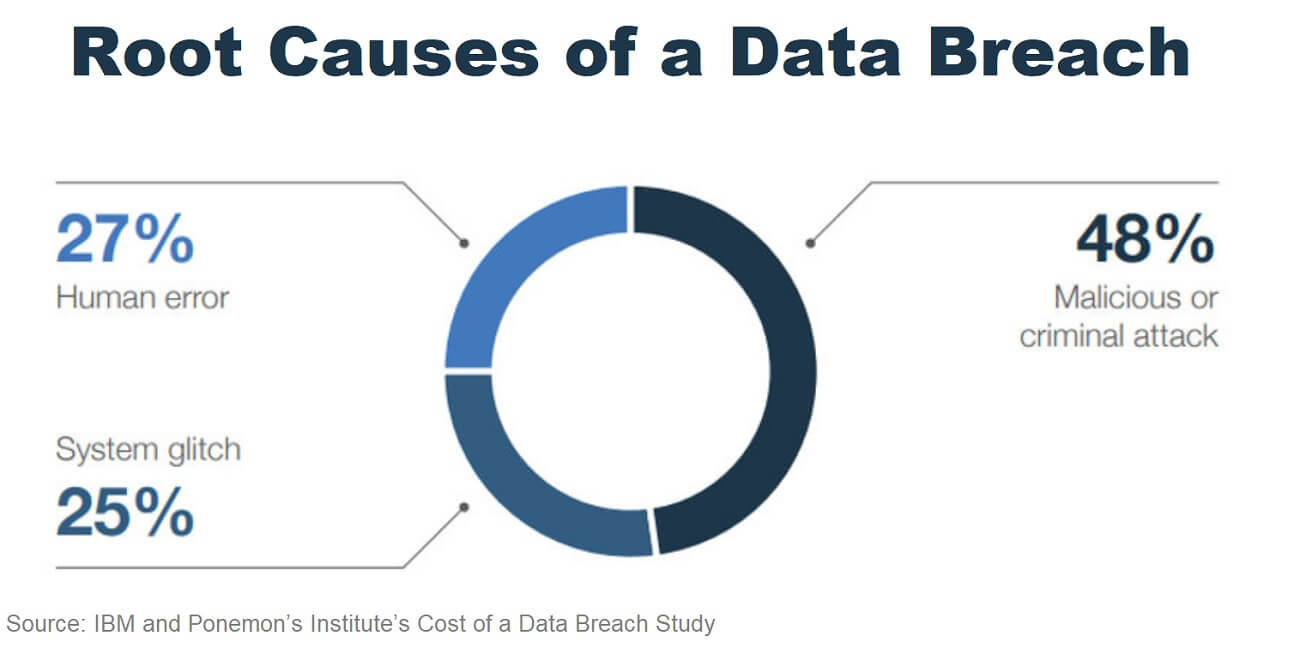

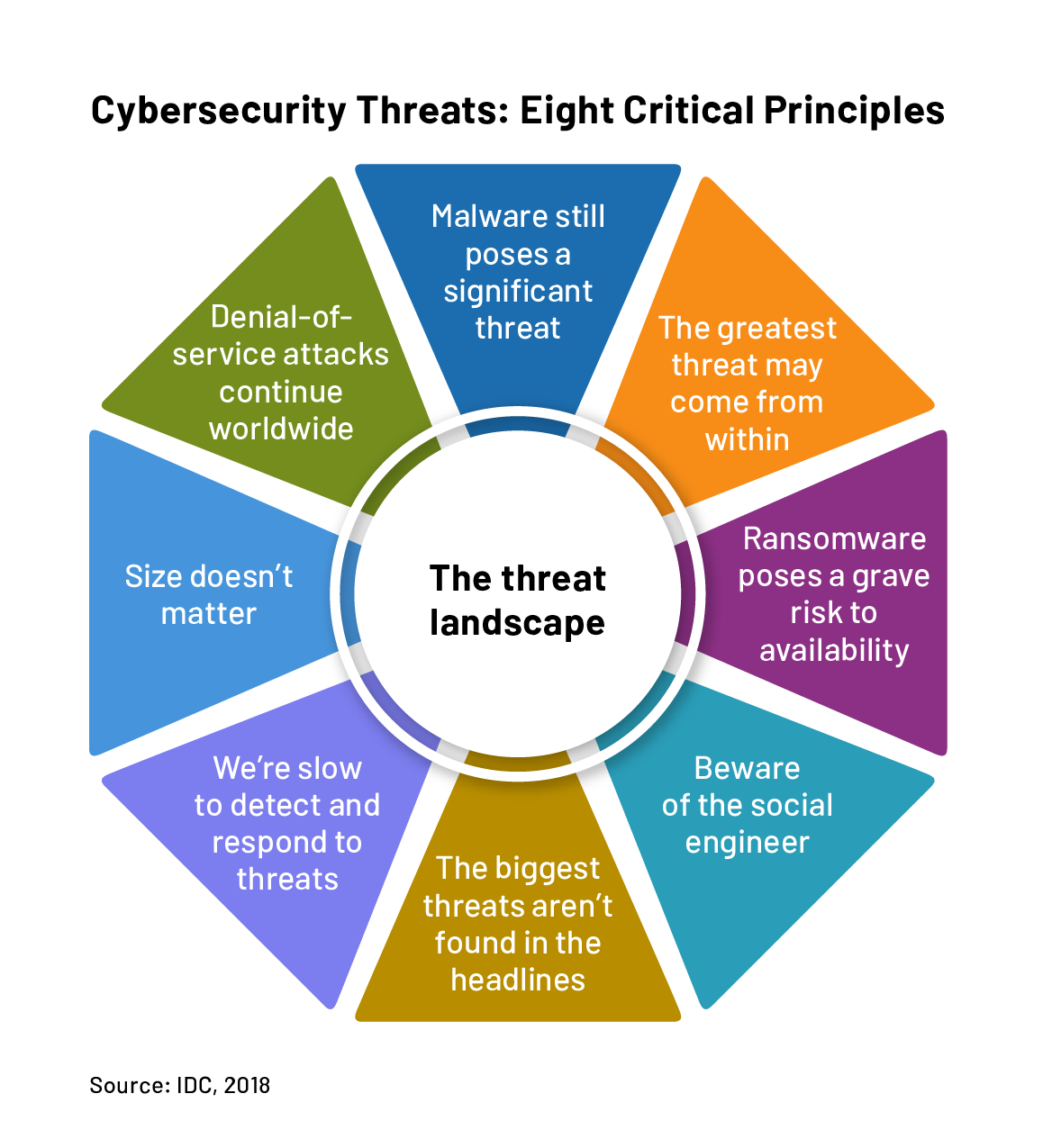
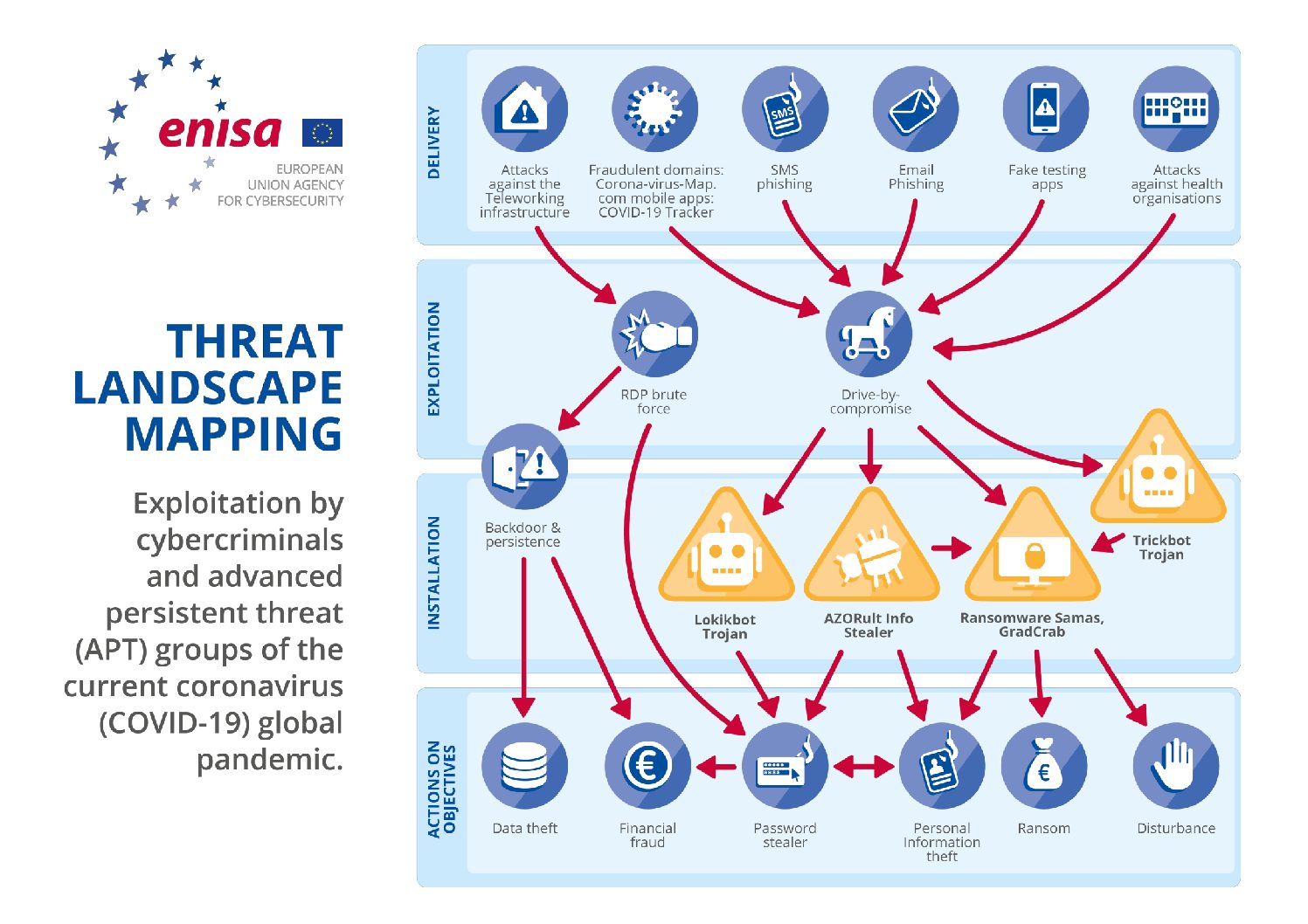


Closure
Thus, we hope this article has provided valuable insights into The Evolving Landscape of Game Security: A Look at Potential Vulnerabilities in 2025. We appreciate your attention to our article. See you in our next article!